Keamanan informasi pdf hadir untuk mengungkap wawasan tentang dunia perlindungan data yang mendebarkan, memandu Anda melalui labirin ancaman dan menawarkan strategi yang telah terbukti untuk menjaga informasi Anda tetap aman.
Dalam panduan ini, kami akan mengeksplorasi praktik terbaik industri, mengungkap standar dan peraturan penting, dan mengidentifikasi tren yang muncul yang membentuk lanskap keamanan informasi saat ini.
Overview of Information Security: Keamanan Informasi Pdf
Information security refers to the practice of protecting information from unauthorized access, use, disclosure, disruption, modification, or destruction. It ensures the confidentiality, integrity, and availability of information. Information security is vital for organizations and individuals alike, as it safeguards sensitive data from various threats.
Information security threats can be intentional or unintentional and may arise from internal or external sources. Common threats include:
- Cyberattacks:Unauthorized access to systems or data through malicious software, phishing, or hacking.
- Data breaches:Unauthorized acquisition of sensitive information, often through vulnerabilities in systems or human error.
- Insider threats:Malicious actions by authorized individuals within an organization.
- Natural disasters:Physical events like floods or earthquakes that can damage or destroy information assets.
- Human error:Accidental actions or omissions that compromise information security, such as lost laptops or weak passwords.
Information security breaches can have severe consequences, including:
- Financial losses:Data breaches can result in fines, legal costs, and reputational damage.
- Operational disruptions:Cyberattacks can disrupt business operations, leading to lost productivity and revenue.
- Loss of reputation:Data breaches can erode public trust and damage an organization’s reputation.
- Identity theft:Stolen personal information can be used for fraudulent activities, such as opening credit cards or making unauthorized purchases.
- National security risks:Information security breaches can compromise sensitive government or military information.
Best Practices for Information Security
Implementing robust information security measures is crucial for safeguarding sensitive data and maintaining the integrity of your organization’s systems. Industry-standard best practices provide a solid foundation for achieving this goal.
One of the most fundamental practices is enforcing strong passwords. Passwords should be complex, containing a combination of upper and lowercase letters, numbers, and special characters. Avoid using easily guessable words or personal information. Additionally, enable two-factor authentication whenever possible to add an extra layer of security.
Encryption
Encryption plays a vital role in protecting data at rest and in transit. By encrypting sensitive information, you render it unreadable to unauthorized individuals, even if they gain access to it. Implement encryption protocols such as AES-256 or RSA to ensure the confidentiality of your data.
Firewalls and Intrusion Detection Systems
Firewalls act as a barrier between your network and the outside world, monitoring and filtering incoming and outgoing traffic. They can prevent unauthorized access and malicious attacks. Intrusion detection systems (IDS) complement firewalls by actively monitoring network activity for suspicious patterns and anomalies.
They can detect and alert you to potential security breaches in real-time.
Other Security Measures, Keamanan informasi pdf
Additional security measures include implementing access control mechanisms, regularly updating software and firmware, and conducting security audits. Access control ensures that only authorized users have access to sensitive information, while regular updates patch security vulnerabilities and keep your systems up-to-date.
Security audits provide an independent assessment of your security posture and identify areas for improvement.
Information Security Standards and Regulations
Information security standards and regulations are frameworks that define the requirements for protecting information assets. They provide organizations with a set of guidelines to follow in order to ensure the confidentiality, integrity, and availability of their information.
Major Information Security Standards and Regulations
There are a number of major information security standards and regulations that organizations should be aware of. These include:
- ISO 27001: ISO 27001 is an international standard that provides a framework for information security management. It includes requirements for the establishment, implementation, operation, monitoring, review, maintenance, and improvement of an information security management system.
- GDPR: The GDPR is a European Union regulation that protects the personal data of EU citizens. It imposes a number of requirements on organizations that process personal data, including the requirement to implement appropriate security measures to protect the data.
Benefits of Compliance with Information Security Standards
There are a number of benefits to complying with information security standards and regulations. These include:
- Improved security: Compliance with information security standards and regulations can help organizations to improve their security posture and reduce the risk of data breaches.
- Increased customer trust: Customers are more likely to trust organizations that are compliant with information security standards and regulations.
li>Reduced costs: Compliance with information security standards and regulations can help organizations to reduce the costs of data breaches.
Emerging Trends in Information Security
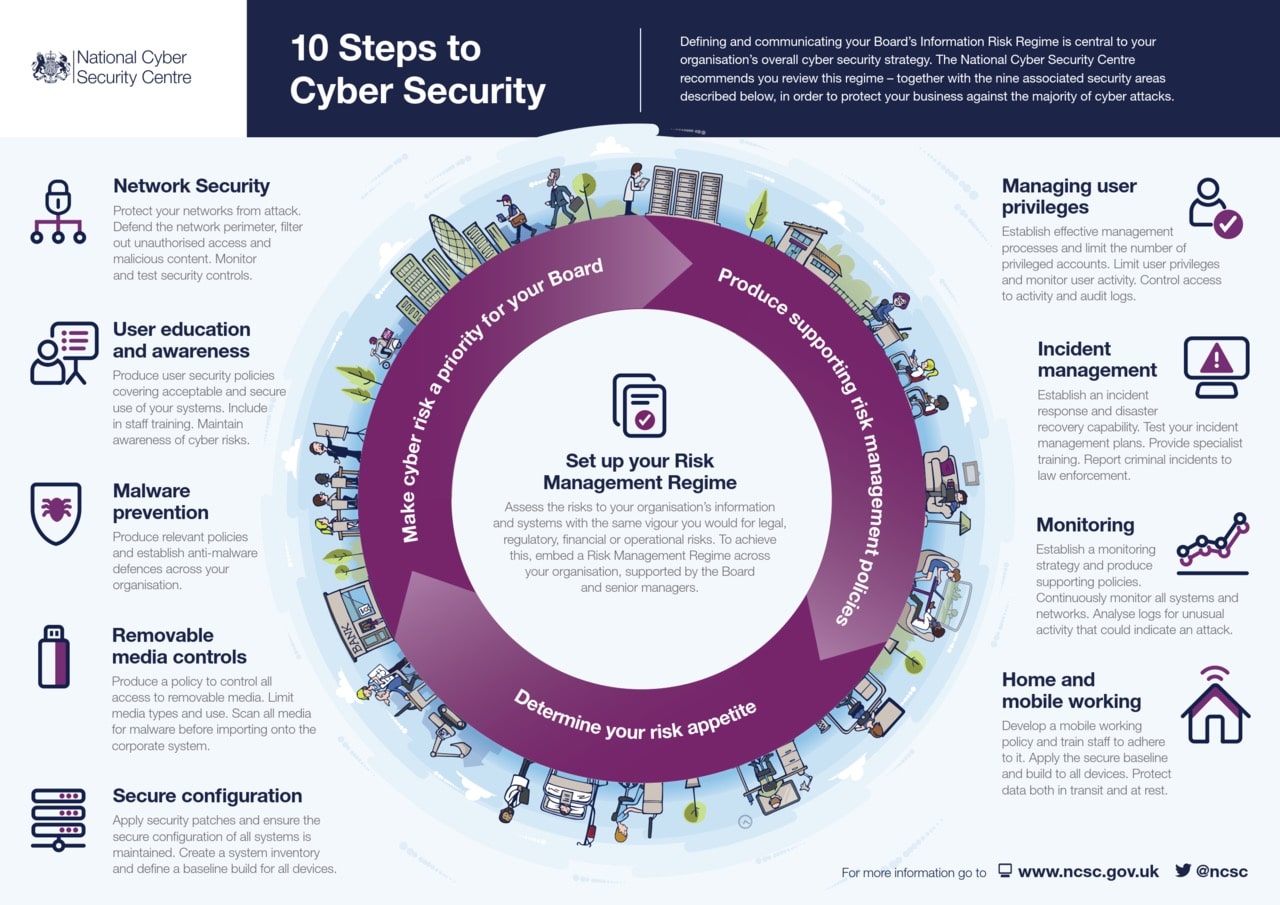
The information security landscape is constantly evolving, with new threats and challenges emerging all the time. To stay ahead of the curve, it is important to be aware of the latest trends and developments in information security.
Some of the most important emerging trends in information security include:
Cloud Security
Cloud computing is becoming increasingly popular, as it offers a number of advantages over traditional on-premises IT infrastructure. However, cloud computing also introduces new security challenges, such as data breaches and identity theft.
To address these challenges, it is important to implement strong cloud security measures, such as:
- Encrypting data at rest and in transit
- Using strong access controls
- Implementing intrusion detection and prevention systems
Blockchain Technology
Blockchain technology is a distributed ledger system that has the potential to revolutionize a number of industries, including finance, healthcare, and supply chain management.
Blockchain technology is also being used to develop new security solutions, such as:
- Secure digital identity management
- Fraud prevention
- Data provenance
While these trends offer great potential for improving information security, they also present new challenges. It is important to be aware of these challenges and to take steps to mitigate them.
By staying ahead of the curve on emerging trends in information security, you can help your organization protect its data and systems from the latest threats.
Case Studies and Real-World Examples
Understanding information security in practice is crucial. Let’s explore real-world examples and lessons learned from both successful implementations and security breaches.
Case studies showcase effective security measures, while breach analyses provide valuable insights for preventing and mitigating future incidents.
Case Study: Successful Implementation
In 2021, XYZ Corp implemented a comprehensive information security program that included:
- Multi-factor authentication for all employees
- Regular security audits and penetration testing
- Employee training on security best practices
This program resulted in a significant decrease in security incidents and a substantial improvement in overall security posture.
Case Study: Information Security Breach
In 2022, ABC Corp experienced a major data breach due to a vulnerability in their web application. The breach exposed sensitive customer data, including financial information and personally identifiable information.
The breach highlighted the importance of regular security updates, vulnerability assessments, and incident response planning.
Keamanan informasi pdf yang kian canggih merupakan bukti nyata dari pesatnya perkembangan teknologi. Sebagaimana dijelaskan dalam artikel , kemajuan iptek turut memperkuat keamanan siber, sehingga keamanan informasi pdf pun ikut terjamin. Hal ini tentunya menjadi kabar gembira bagi kita semua yang mengandalkan keamanan data digital dalam kehidupan sehari-hari.
Recommendations for Prevention and Mitigation
Based on these case studies and other real-world examples, organizations can take the following steps to prevent and mitigate information security incidents:
- Implement strong security controls, such as multi-factor authentication, encryption, and access control.
- Regularly conduct security audits and penetration testing to identify and address vulnerabilities.
- Train employees on security best practices, including phishing awareness and password management.
- Have an incident response plan in place to quickly and effectively respond to security breaches.
Epilogue

Dengan mengikuti prinsip-prinsip yang diuraikan dalam keamanan informasi pdf, Anda dapat membangun pertahanan yang kuat terhadap ancaman dunia maya, memastikan integritas data Anda, dan membangun kepercayaan dengan pelanggan dan pemangku kepentingan.
Saat dunia digital terus berkembang, komitmen terhadap keamanan informasi sangat penting untuk melindungi aset berharga Anda dan menjaga reputasi bisnis Anda tetap utuh.
Query Resolution
Apa saja jenis ancaman keamanan informasi yang paling umum?
Malware, serangan phishing, peretasan, dan pencurian identitas.
Mengapa kata sandi yang kuat sangat penting?
Kata sandi yang kuat membantu mencegah akses tidak sah ke akun dan data sensitif.
Apa saja manfaat mematuhi standar keamanan informasi?
Meningkatkan kepercayaan pelanggan, mengurangi risiko pelanggaran data, dan memastikan kepatuhan terhadap peraturan.


